 Your website is overloaded, You are getting database error, website is not available messages. Your customers are calling your employees and complaining about website. You and your employees are in panic. Well your website is attacked by a method called Ddos.
Your website is overloaded, You are getting database error, website is not available messages. Your customers are calling your employees and complaining about website. You and your employees are in panic. Well your website is attacked by a method called Ddos.
This article will explain you Ddos and step by step explanation to deal with Ddos and prevent it in future
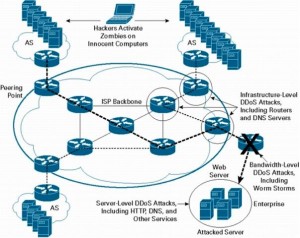
Distributed Denial of service (Ddos) attack is a method, used by disgruntled competitors to destroy the other party’s website and deny the web service to his potential customers.Some time hackers and groups use it prove their point. This attack flood your server with traffic and ping, and the server will be overloaded. This will lead to webserver is not available, Unable to connect with database etc errror to potential customers. Some time the server will crash due to overload. To understand what is DDos, I think you must know what is Dos attack.
What is Denial of service attack
Dos attack means Denial of service attack. For example your business may be doing very good and it is growing. You competitor may be jealous and they want to harm your business, so that they can eat your lunch. So some time your competitor may try to harm your business in unethical way. They may try to deny your website to your potential customers by flooding your server with trafic and datas. Your server become too busy and it may not respond to your potential customer. This is called DOS attack (denial of service attack).
We can prevent dos by simply blocking the ip address that is try to ping you repeatedly.
what is ddos
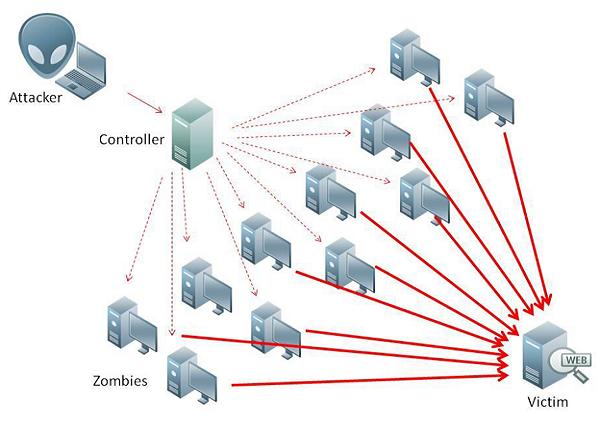
But now the attackers have developed more complicated and sophisticated method for dos attack. That is called Distributed Denial of Service attack (Ddos). For this first they prepare 100’s or 1000’s of zombie Computers. They do this by infecting millions of unprotected computers over the internet. Even the computer owners may not aware that their system is compromised and using as zombi computer for a Ddos. Some time the zombie agent installed in these computer, may be hard coded with your websites IP address and time. Some time the compromised computers may be in the control of the attacker, so that he can use these machines to multiple attacks.
Once these zombie computers are ready, the attacker may unleash the attack on your server. suddenly 100’s or 1000’s computers will start pinging with your server, making it to crash. Thus your potential customers can not access your website.
Image source: http://nsfocusblog.com/2012/10/29/ddos-attack-and-defense/
How to stop ddos attacks
It is virtually impossible to prevent DDOs attack manually, as there will 1000’s of IP’s involved in it. You can not recognize who is the attacker and who is the real customer. One of the best way is to install a firewall and configure that to prevent DDOS.
Recently I used the following Firewall to prevent a ddos attack on one of my website. The attack has literally taken the website out of internet. Myself and the visitors were getting only “website is not available” message. When I logged in to the system, the CPU was 100% loaded and 1000’s of process were going on.
how to prevent ddos attacks
I have used the following firewall to stop or kill the ddos attack against me. The firewall has blocked exactly 200 ip address that shows me that this was a planned attack.
The firewall I used was this
You can ask your webhost to add this firewall or you can add it yourself if you good at linux.
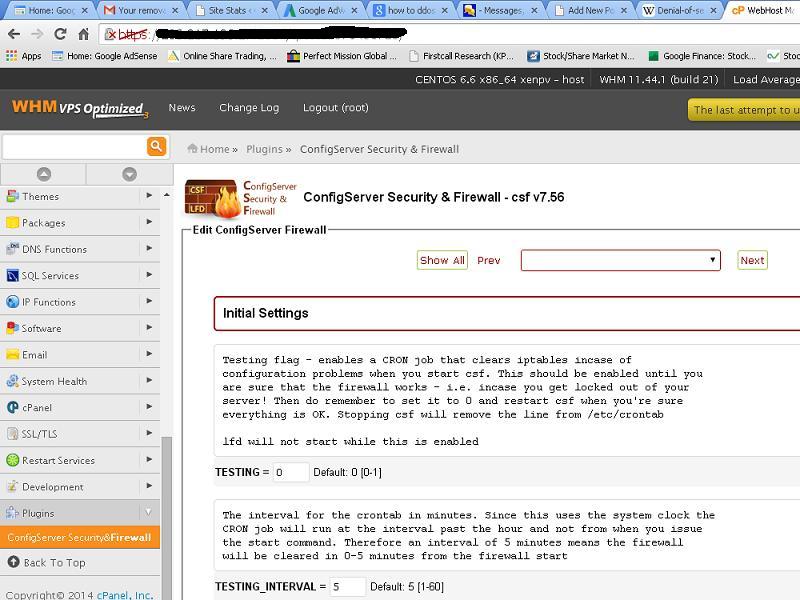
Log in to WHM
Once it is done, go to your web hosting manager (not to control panel), and open the plugin.
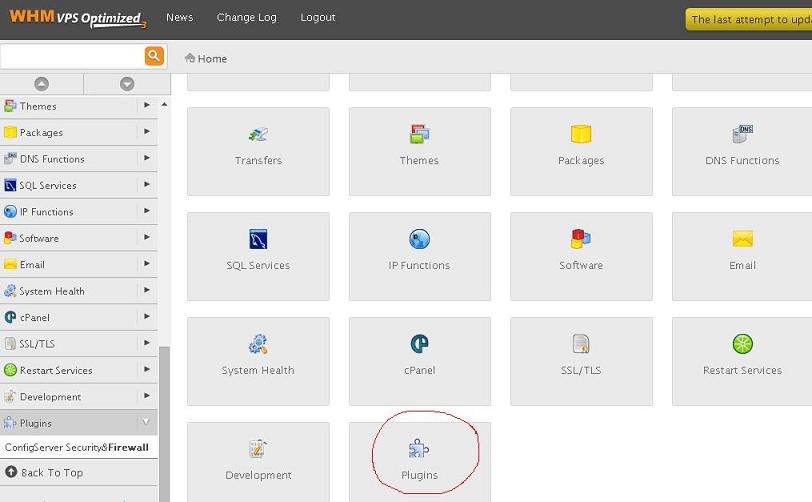
2. You will see the link to the plugins. Please click on this link
WHM plug in screen
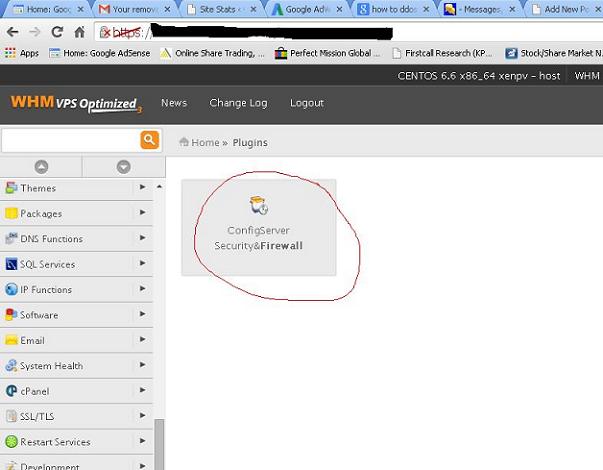
You will reach to plugin screen and you can see config server plugin. Please click on this link
Welcome screen of config server firewall
You will see the welcome screen of config server firewall.
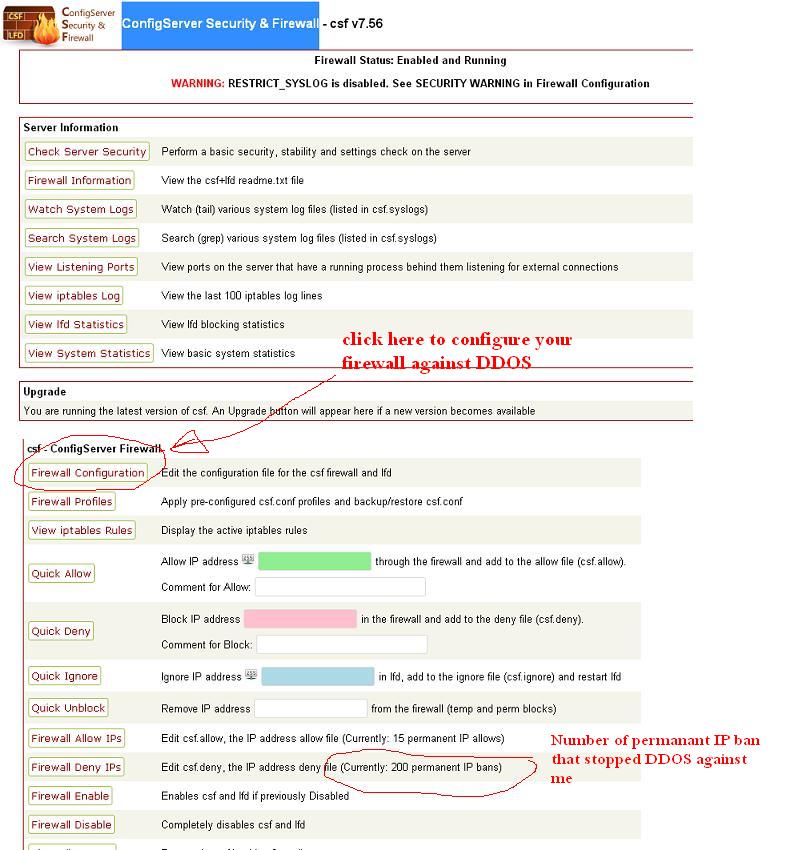
You can see that my firewall ha blocked 200 IP’s permanently on my server.Firewall detected these IP’s as abusing my server.
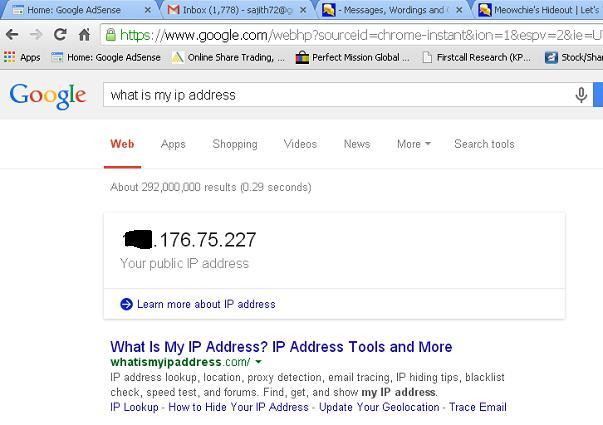
Look up your Ip Address in google
Better to whitelist your IP, so that you wont get blocked by firewall, while testing and configuring your firewall.
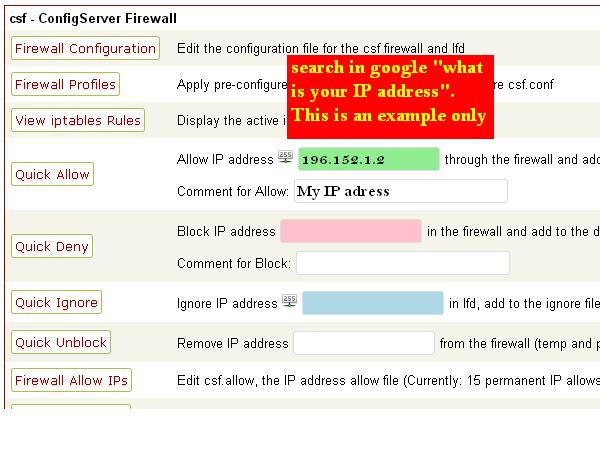
Allow your IP address in firewall
Type your IP in green box, add comment and click quick allow. This will allow your IP permanently.
Configurations of CSF firewall
Click on the firewall configuration button
You will see Config server firewall configuration page.
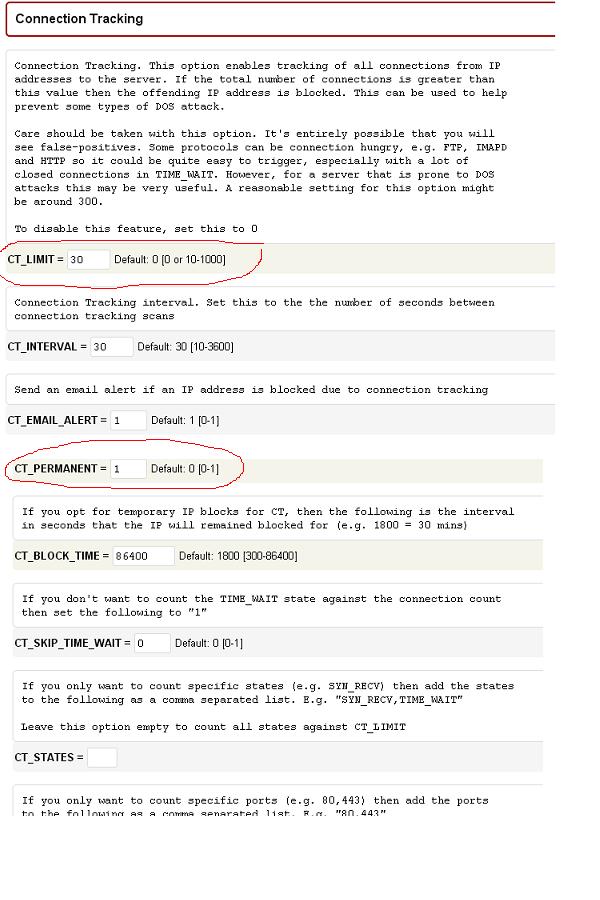
Connection tracking and firewall setting
Now search for connection tracking. Modify the following. I had tried with 50,40,30 and with 20. You may have to try with different setting so that the firewall can correctly detect the abusing IP’s. I have tried with 50 first and the firewall has detected only one IP. Then I have tried with 40, and my own IP got blocked. I had to contact web host to white list me, in order to continue. That is why I have asked you to whitelist your IP before continuing.Then I have changed to 30, and after 2 hours, the number of blocked IP has become 200 and it stopped there
I have tried with 20 also, but the server was not detecting any extra abusing IP’s. I think the attacker has limited around 35 connection per IP. So if your attacker has limited 19 connection per IP, then the firewall will not be able to identify the attacking IP’s, even if you set 20. Then you may have to try by limiting connections to 20. So i recommend you to try with different settings, until your firewall detect all abusing IP’s and block them permanently.
I have searched to find optimum number of connections required to run a website properly. What is my understanding is that some protocols are really connection hungry and it is not a good idea to limit the connections to low number.
Now your firewall is configured to stop DDOS, by blocking IP’s that is trying to abuse your server.
The above setting is enough to prevent DDOS attack. But if you are still getting attacked then you can do the following settings also
I also recommend you to consider cloudflare service, so that your server load will reduce considerably.
If you like the above post please do not forget to share it with your friends and colleagues in twitter and facebook
from distributed IP addresses to a specific application account. If the
number of failures matches the trigger value above, ALL of the IP addresses
involved in the attack will be blocked according to the temp/perm rules aboveTracking applies to LF_SSHD, LF_FTPD, LF_SMTPAUTH, LF_POP3D, LF_IMAPD,
LF_HTACCESSSECURITY NOTE: This option is affected by the RESTRICT_SYSLOG option. Read
this file about RESTRICT_SYSLOG before enabling this option: